Cyber Attack, Disability and Smile Minimal Line Icons. for Web Application, Printing. Neon Laser 3d Lights. Vector Stock Vector - Illustration of chat, social: 248087457

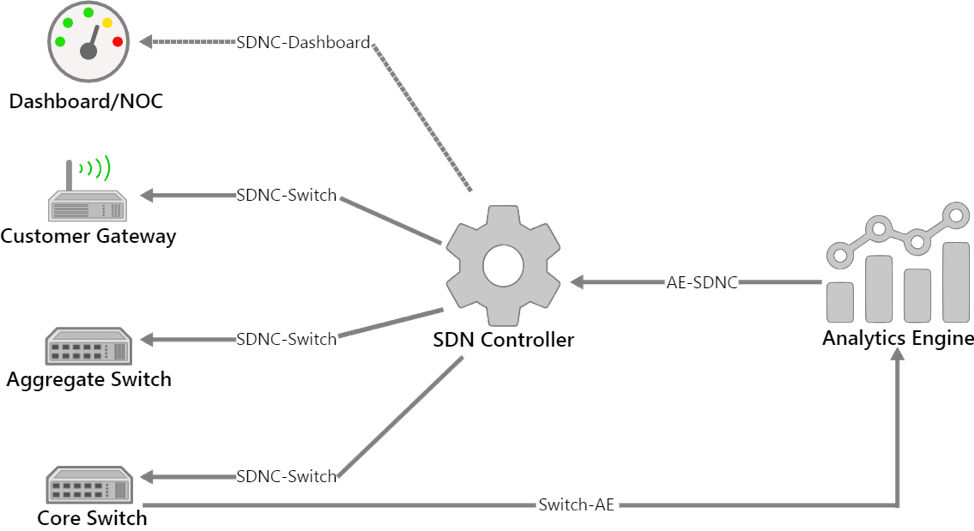
a) SDN/QKD Optical Network testbed. b) DoS attacker for links 1 and 2.... | Download Scientific Diagram